What Is a Cybersecurity Management Platform? Key Insights
Jan 17, 2025

Key Takeaways
- Cybersecurity management platforms combine features like threat detection, risk management, and compliance tracking into a single system, making it easier to protect data and networks.
- These platforms provide real-time monitoring and automated responses to quickly address potential threats.
- The right platform should fit your organization's size and security needs, offering flexibility as your business grows and evolves.
In a time when the internet comprises a whirlwind of data and information, cybersecurity management is just what industry leaders need to safeguard against cyber attacks.
So, as cyberattacks become more frequent and complex, having a cybersecurity management platform is critical to help manage risks and respond quickly to potential breaches.
Read on to learn more about these platforms and how to choose the right one!
What Is a Cybersecurity Management Platform?
A cybersecurity management platform is a software solution that helps protect organizations from digital threats. It combines various tools and services into one system to monitor, assess, and manage security across computers, networks, and data.
This platform works by gathering information from different sources, like firewalls, antivirus programs, and detection systems, to provide a clear overview of the organization's security status. It can identify vulnerabilities, track potential threats, and respond quickly to attacks.
If a threat is detected, the platform can automatically alert the team, block harmful activities, or fix weak points. This way, a cybersecurity management platform helps businesses run smoothly without being disrupted by security risks.
Cybersecurity Management Platform Types
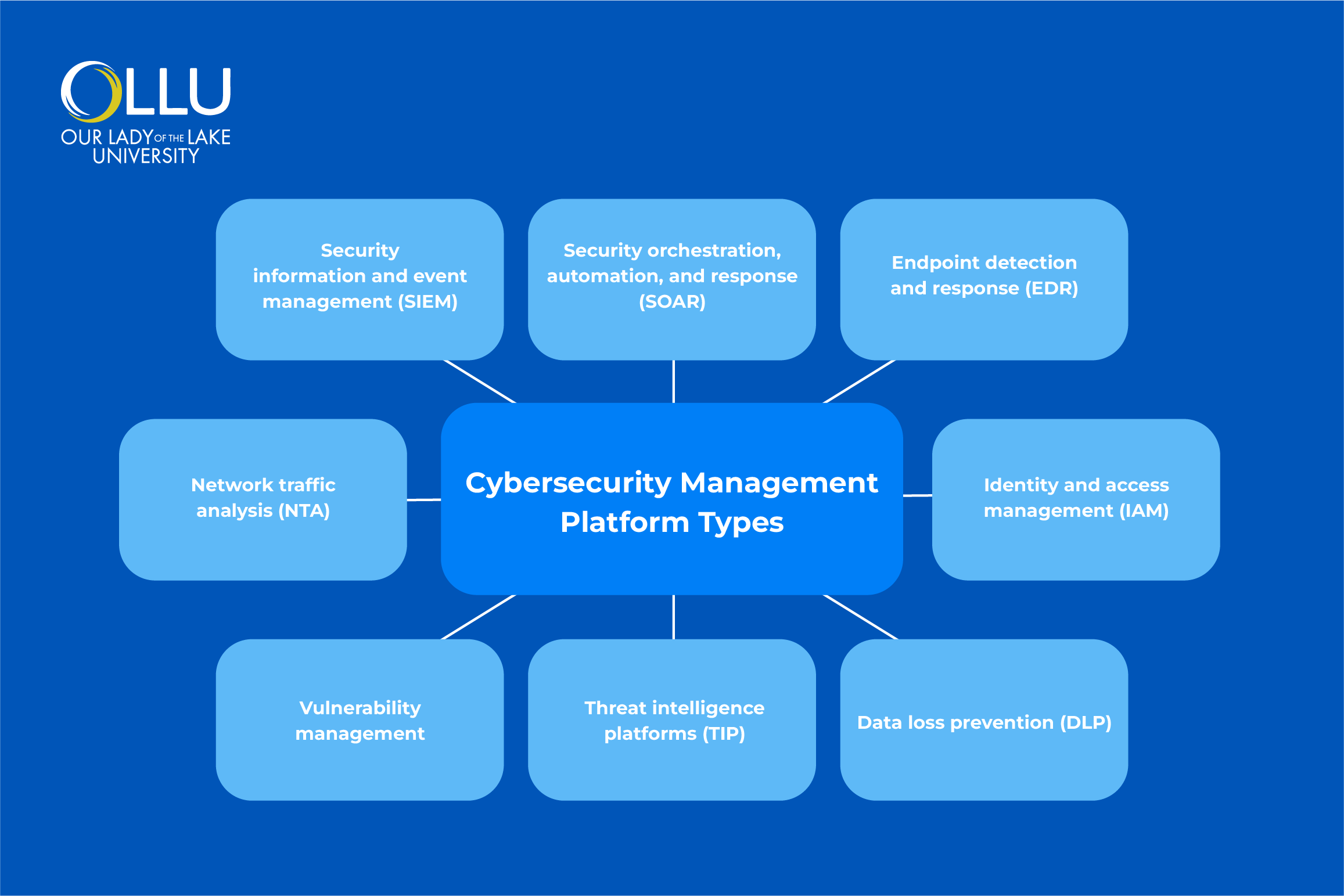
There are many types of cybersecurity management platforms, each targeting a different
aspect of protection across systems, networks, and data.
Security information and event management (SIEM)
SIEM collects and reviews security data from different sources to spot threats and send alerts. It helps monitor activity, investigate incidents, and meet security guidelines. By providing a centralized view of security, SIEM makes it easier to identify and respond to complex attacks.
Security orchestration, automation, and response (SOAR)
Central to the SOAR platform is the automation of security tasks, like threat response and mitigation, to simplify the process. It helps save time, reduce errors, and improve security team efficiency. SOAR also integrates multiple security tools, enabling teams to act faster during an incident.
Endpoint detection and response (EDR)
EDR protects devices like computers and smartphones by watching for unusual activity, stopping threats, and fixing issues. It's great for handling malware and hacking attempts. EDR continuously monitors endpoints, ensuring any suspicious behavior is detected early.
Identity and access management (IAM)
IAM controls who can access systems and data. It ensures the right people have access while keeping others out, improving security and usability. IAM also strengthens security by enforcing policies like multi-factor authentication.
Network traffic analysis (NTA)
NTA checks network activity to find unusual patterns or attacks. It's useful for spotting hackers or data theft in progress. As such, NTA provides early warnings of potential breaches by analyzing real-time traffic.
Vulnerability management
This platform identifies security weaknesses in systems and software, prioritizing vulnerabilities according to their risk levels and offering recommendations for security remediation. It serves as an essential tool, helping organizations stay ahead of emerging threats through regular scanning and reporting.
Threat intelligence platforms (TIP)
TIP collects information about new cyber threats. It helps businesses prepare for attacks and share warnings with their security tools. TIP also provides insights that help security teams predict and prevent future risks.
Data loss prevention (DLP)
DLP prevents sensitive information, like financial data, from being leaked and shared or accessed improperly. It focuses on protecting important data from unauthorized access or transfer. DLP also monitors data use to ensure compliance with privacy regulations.
Key Features
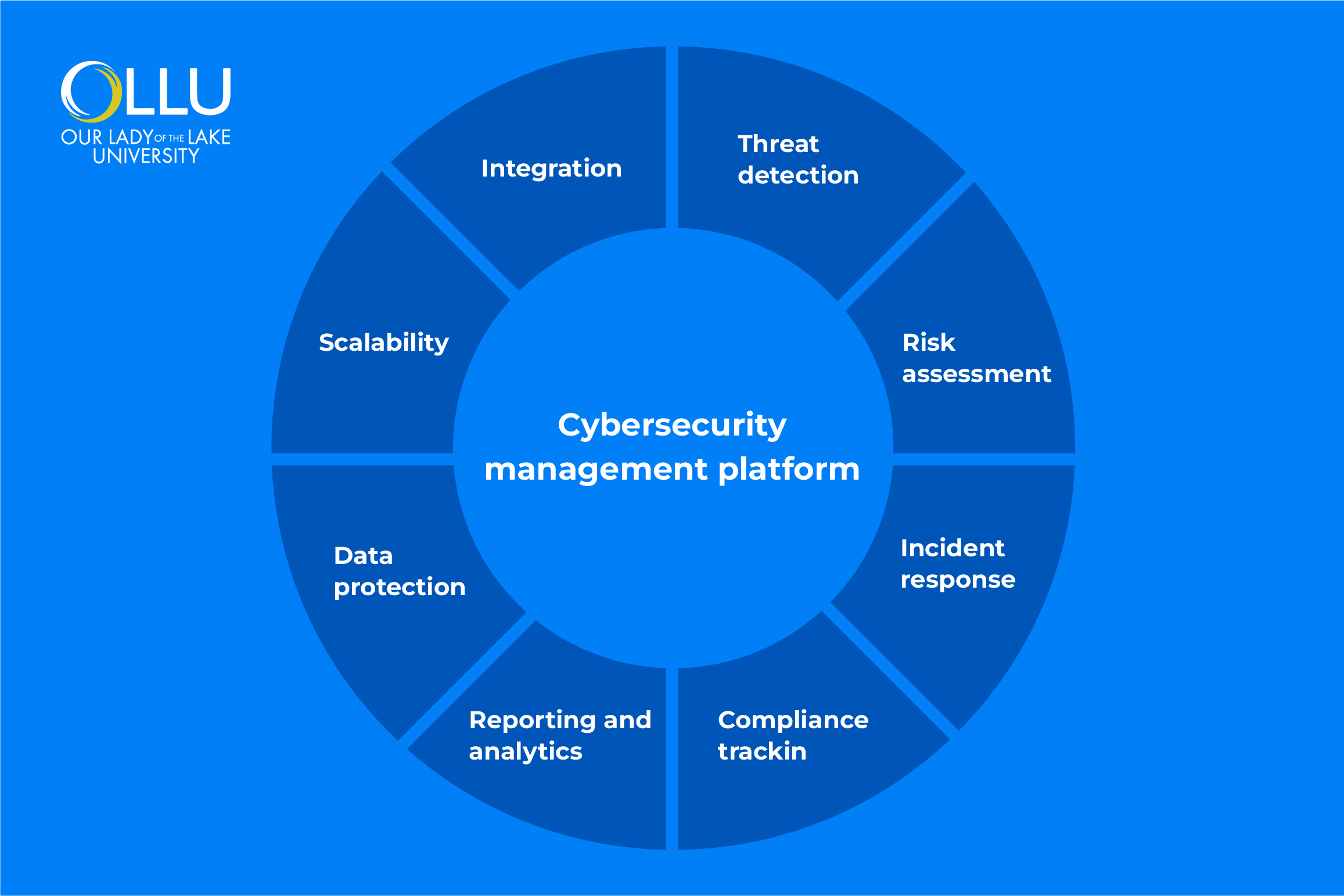
Cyber security management platforms employ a multilayered approach to network protection,
encompassing multiple key features, such as:
- Threat detection: Monitoring for unusual activities to identify potential threats, like malware or real-time hacking attempts.
- Risk assessment: Analyzing vulnerabilities in systems and software, helping prioritize what needs to be fixed.
- Incident response: Automating and streamlining how organizations respond to attacks, ensuring quick action to minimize damage.
- Compliance tracking: Making sure businesses meet security regulations by monitoring and reporting on compliance requirements.
- Reporting and analytics: Providing detailed reports and dashboards to track security performance and incidents over time.
- Data protection: Guarding sensitive information by preventing unauthorized access or data leaks.
- Scalability: Adapting to the organization's size and needs, from small businesses to large enterprises.
- Integration: Working seamlessly with existing tools like firewalls, antivirus software, and cloud platforms for a unified security approach.
These features work together to give organizations a complete view of their security, improve efficiency, and stay ahead of evolving cyber threats. A strong platform not only protects systems but also helps businesses grow securely.
Why Are Cybersecurity Management Platforms Essential?
Organizations need cybersecurity management platforms to protect themselves from cyber threats, which are becoming more frequent and complicated. Hundreds of cyber attacks occur every day, worldwide, emphasizing the need for cybersecurity management.
Just in 2023, the total number of data compromises in the U.S. mounted to 3,205 cases, with over 350 million people affected. Additionally, the cost of data breach in 2024 went to a staggering 4.88 million USD, which is 10% higher than last year.
Cybercriminals use advanced tools, such as AI-powered attacks, to steal data, disrupt systems, and cause financial damage. Cybersecurity management platforms help detect threats in real time, fix weak spots in systems, and quickly respond to incidents, keeping businesses safe.
They also help organizations follow security laws and industry rules, avoiding fines and protecting their reputation. Cybersecurity tools reduce risks by preventing hackers from accessing sensitive information like customer data or company secrets.
These and other benefits make such platforms vital. They allow companies to stay ahead of evolving threats and operate securely.
Choosing the Right Cybersecurity Management Platform

To choose the right cybersecurity management platform, you need to consider your
organization's size, industry, and specific security needs. Smaller businesses might
prioritize cost-effective, user-friendly solutions, while larger organizations may
need advanced tools with scalability and integration options.
Identify your primary security concerns—such as protecting sensitive customer data, preventing cyberattacks, or meeting compliance requirements—and look for platforms specializing in those areas. For instance, industries like healthcare or finance may need platforms focused on data protection and regulatory compliance.
Evaluate ease of use and training requirements. A complicated system might slow down response times, especially for smaller teams. Ensure the platform integrates well with your existing tools, like firewalls or cloud services, for a seamless operation.
Lastly, check reviews, vendor support, and scalability. As threats grow, your platform should adapt to handle increasing demands. Always choose a solution that balances features with your organization's budget and goals.
The Bottom Line
Using a cybersecurity management platform is essential for staying ahead of growing cyber threats, as these tools help detect, respond to, and prevent real-time attacks. With the increasing complexity of cyberattacks, having the right platform is more important than ever. If you're looking to safeguard your business, make sure to assess your needs—such as the size of your business, specific security concerns, and industry regulations—and choose a platform that offers the right features, scalability, and ease of use.
Additionally, as the need for cybersecurity professionals with advanced skills grows, a career in cybersecurity can be a wise choice. You can check OLLU's Computer Information Systems and Security (CISS) programs to become prepared for a wide range of information systems and technology jobs in all industries. Or consider a Master's program in Cybersecurity or Master's in Cybersecurity Management to equip yourself with the skills and knowledge necessary to fight cyber threats and lead others in protecting the digital world.
Frequently Asked Questions (FAQs)
What is the difference between cybersecurity and cybersecurity management?
Cybersecurity focuses on protecting systems, networks, and data from cyber threats, while cybersecurity management involves overseeing and coordinating the processes, tools, and teams that handle security activities.
What is an example of a security platform?
A common example is security information and event management (SIEM), which collects and analyzes security data to identify and respond to potential threats.